 Millions of people are unaware of how their personal data is being collected, used, or shared in our increasingly digital society. As a business, it’s more important than ever to have a data privacy strategy to protect customers and employees and remain compliant with applicable regulations.
Millions of people are unaware of how their personal data is being collected, used, or shared in our increasingly digital society. As a business, it’s more important than ever to have a data privacy strategy to protect customers and employees and remain compliant with applicable regulations.
In an era of heightened risk and uncertainty, remote workforces, and complex technologies, having effective policies and procedures that are easy-to-understand and accurate has become critical to keeping pace in the developing global regulatory landscape.
Data Privacy and Protection - Why Is It Important?
Data privacy is the set of strategies and processes that focus on how personal data is collected, processed, stored, shared, retained, and destroyed. In contrast, data protection focuses on securing the availability and integrity of data and protecting assets from unauthorized access. A data privacy and protection strategy are crucial for any organization because it aims to provide individuals with transparency, control over their data and how it is used, and to protect personal data from unintended access and use. Without a data privacy and protection strategy, your organization may be more vulnerable to consumer complaints, regulatory investigations and fines, and fraudulent activities like identity theft, phishing, and hacking.
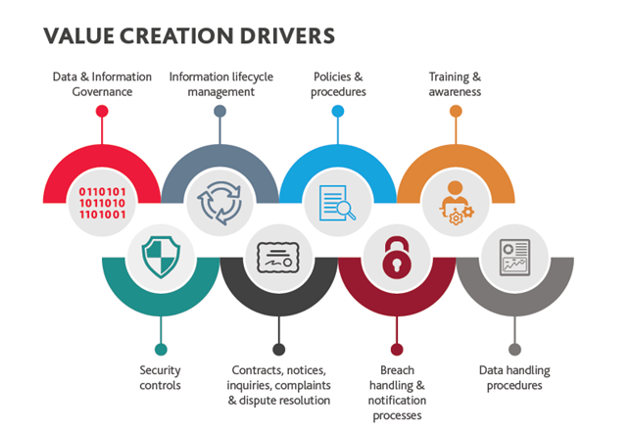
Source: https://www.bdo.com/services/business-financial-advisory/governance,-risk-compliance/data-privacy
Components of a Data Privacy and Protection Strategy
When developing a strategy, you need to understand:
The Business
Understanding the business is key to a data privacy and protection program. The more you know about the business, the more you’ll understand about the types of data it processes and the level of protection required, and so on.
The Data
Many organizations collect personal data from both internal and external sources. For example, a bank collects financial information from customers. A healthcare organization collects health information. All organizations collect and process personal data of their employees. It’s important to identify the categories of personal data as this will inform various privacy notices, policies, and procedures.
The Purpose
It’s one thing to identify data, but to understand what the data is and how it serves a purpose in your organization is an entirely different task. This is important when building a data privacy and protection strategy because it helps you populate your personal data inventories and records of processing (where applicable or legally required), identify opportunities for data minimization, confirm that the data collected is proportional to the purpose, and implement appropriate safeguards.
Data Privacy and Protection—5 Steps to Get Started
Identifying data, how that data is used, classifying the data, and outlining what actions to take with each type of data is key to data privacy. Here are five things all organizations can do to begin or enhance their data privacy strategy:
1. Identify where your data is located
It can be a challenging task but identifying where your data is should be the first step in protecting it. Where does all your data live, and where does it go? What types of data exist? Where is it physically hosted? Discovering your data is a foundational task because it informs the rest of your data privacy and protection strategy.
2. Identify what your data is
You cannot protect your data without first understanding what you have. After identifying where the data is, the next step is to create a personal data inventory and record what you do with that data. At this stage, you may also tag the data by classification. Data classification helps to organize the data into groups – most often according to the level of sensitivity - to enable efficient data protection.
It’s also important to note that data protection and e-discovery have a certain functional overlap and that we see a rise in privacy programs leveraging e-discovery solutions as part of their privacy strategy and toolsets. Data investigation is also less burdensome when your data is classified; therefore, the two can be interdependent.
3. Determine who has access to the data
Who currently has access to each type of data? This includes internal stakeholders, as well as third-party recipients, such as service providers or partners. Knowing who is receiving or accessing the data and where they are located affects the rules you’re placing around the data and transfers. Certain privacy laws may also require data localization or additional technical, organization, and contractual safeguards to transfer data cross-border.
4. Define how you will implement privacy controls
Once you understand your data, you can better customize privacy policies and procedures. For example, you can use your personal data inventory to guide where and how to execute a data subject/consumer rights request. Understanding your business, technologies, and risk profile can also help you create a customized privacy by design program and methodology that embeds privacy controls during the early stages of a project or development lifecycle.
5. Implement technical and organizational controls
A data privacy strategy relies upon the implementation of strong security controls. This includes organizational or programmatic controls such as policies, training and awareness, incident response plans, and password policies, as well as technical controls such as encryption, anonymization, logging, multi-factor authentication, and vulnerability detection. One important safeguard for data protection is Data loss prevention (DLP) which prevents unauthorized leakage of data outside of the organization. Once data is classified, the technical implementation of DLP can establish policies for each layer of classification to prevent unwanted sharing. Once implemented, continuously monitor and maintain the policies to stay up to date with business needs and regulatory requirements.
For more information on the above article or any business advisory services, contact Melissa Motley, CPA, at (334) 887-7022 or by leaving us a message below.
Written by Taryn Crane, Mark Antalik, and Steve Combs. Copyright © 2022 BDO USA, LLP. All rights reserved. www.bdo.com







